An introduction to information security this introduction to both traditional and recent cryptographic techniques includes over 80 basic programs for writing and cracking many types of codes and ciphers. Search for library items search for lists search for contacts search for a library.
 5 Easy Ways To Create Secret Codes And Ciphers Wikihow
5 Easy Ways To Create Secret Codes And Ciphers Wikihow
If they enemy finds their paper they will see nonsense.

Codes Ciphers And Computers Introduction To Information Security Epub Download. To protect the secrets that they gather spies use codes and ciphers secret ways to write things down. Code operations require a reference of some kind usually referred to as a code book. Worldcat home about worldcat help.
An introduction to information security. They will not recognize the sensitive information that is being shared. Due to the cumbersome nature of transporting and maintaining code books codes have fallen out of general use in modern cryptography in favour of ciphers.
Codes ciphers and computers. In y cipher a becomes y and so on. A cipher pronounced sai fuhr is any method of encrypting text concealing its readability and meaning.
Book by bosworth bruce. To decode the message the person has to be aware which cipher has been used. In g cipher a becomes g b becomes h and so on.
The use of simple ciphers and codes to protect the security of messages. This particular cipher is not very difficult to decipher and hence secret messages do not remain secret for long. It is also sometimes used to refer to the encrypted text message itself although.
Ciphers are substitution of plaintext for ciphertext. Codes ciphers and computers. Codes ciphers and computers.
In common parlance cipher is synonymous with code as they are both a set of steps that encrypt a message. Free shipping on qualifying offers. An alternative less common term is enciphermentto encipher or encode is to convert information into cipher or code.
In cryptography a cipher or cypher is an algorithm for performing encryption or decryptiona series of well defined steps that can be followed as a procedure. Codes are used in other situations as well and not just by spies. Substitution cipher in which a symbol letter or digit stands for another symbol letter or digit.
Introduction to codes and ciphers.
 Cadet Cyber Civil Air Patrol National Headquarters
Cadet Cyber Civil Air Patrol National Headquarters
 The Caesar Cipher Video Khan Academy
The Caesar Cipher Video Khan Academy
 2019s Best Online Cyber Security Certificate Programs Top 30
2019s Best Online Cyber Security Certificate Programs Top 30
 60 Cybersecurity Interview Questions 2019 Update Daniel
60 Cybersecurity Interview Questions 2019 Update Daniel
 Hacking Secret Ciphers With Python A Beginners Guide To
Hacking Secret Ciphers With Python A Beginners Guide To
 Codes Ciphers And Computers An Introduction To
Codes Ciphers And Computers An Introduction To
 Quantum Computation And Its Effects On Cryptography
Quantum Computation And Its Effects On Cryptography
 Pdf Introduction To Information Security Foundations And
Pdf Introduction To Information Security Foundations And
 What Is Quantum Cryptography Its No Silver Bullet But
What Is Quantum Cryptography Its No Silver Bullet But
 Pdf Implementation Of Aes Algorithm For Information
Pdf Implementation Of Aes Algorithm For Information
 Steganography For The Computer Forensics Examiner
Steganography For The Computer Forensics Examiner
 Cyber Security Course Cyber Security Certification Training
Cyber Security Course Cyber Security Certification Training
 New Cybersecurity Projects For Students Science Buddies Blog
New Cybersecurity Projects For Students Science Buddies Blog
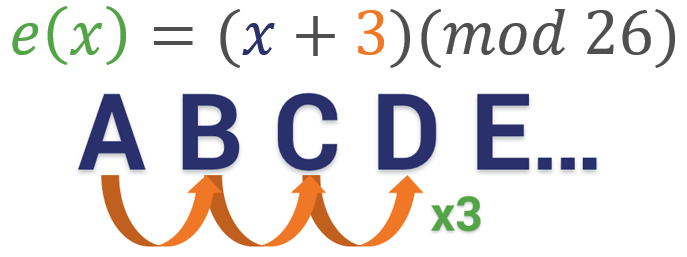 Caesar Ciphers
Caesar Ciphers
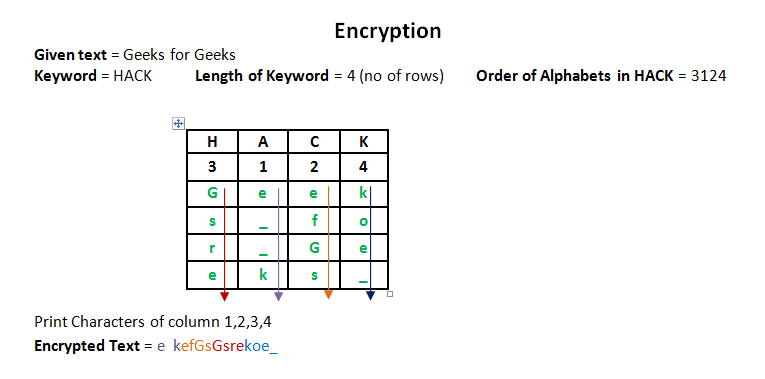 Columnar Transposition Cipher Geeksforgeeks
Columnar Transposition Cipher Geeksforgeeks
0 Response to "Codes Ciphers And Computers Introduction To Information Security Book Depository"
Posting Komentar